SSH is still the backbone of admin work and one of the most scanned services on the Internet. Knocknoc removes SSH from sight entirely and only reveals it after a centralized, authenticated login, adding SSO/MFA or your corporate IdP policies, without changing how engineers connect.
Result: direct, low-latency/non-brokered SSH access with zero pre-auth attack surface for adversaries.
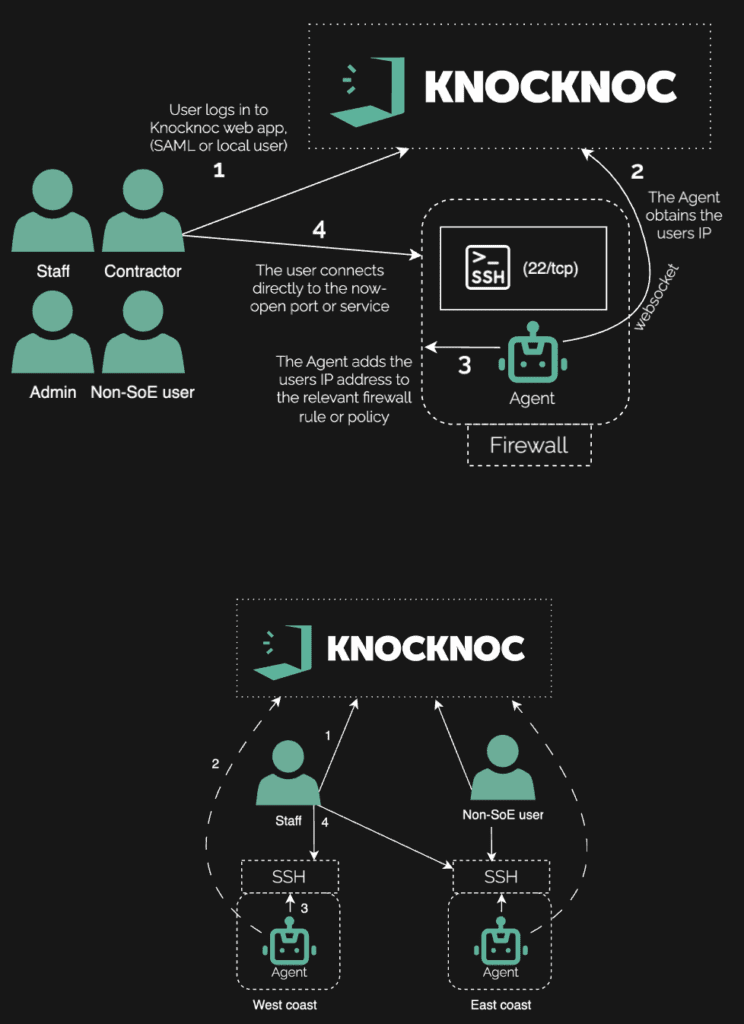
A multinational mining group ran distributed SSH bastion hosts so engineers and external specialists could reach OT sites and distributed systems. The hosts were hammered with brute-force traffic and kept appearing in public scanners. Even with automated banning and strict key use, the CISO worried about a “day-zero before patch-day” scenario.
Security were reviewing constant attack logs. Routing through brokers or a centralized system risked adding latency and points of failure; rolling out client software or changing to ZTNA across contractor devices was unrealistic. The brief was blunt: keep SSH direct and fast, but make it invisible.
Knocknoc added dynamic IP address allowlisting securely and safely to each consuming bastion host. These IPs could then be directly utilized by the mixture of Linux firewalls scripts in use across the environment. Engineers first authenticated to a centralized web application using the organisation’s IdP (with MFA). Only then did Knocknoc dynamically allowlist their IP for port 22 across the bastion hosts; to everyone else, SSH did not exist. No proxies, no rerouting, no client installs.
Scanner noise flatlined. Bastions were no longer discoverable pre-auth. Engineers kept their familiar, direct workflow, now wrapped in SSO/MFA and full auditability, helping close ISO 27001 findings on privileged access, whilst providing a meaningful security uplift
The team is extending the same “just-in-time” control to internal SSH and management networks so privileged access across the estate follows one pattern.
Exposed SSH bastions attract brute-force and day-zero risk. Knocknoc ties SSH network-level exposure to identity: once an engineer completes SSO/MFA, their IP is allowlisted for a short window; otherwise SSH is invisible. No brokers. No rerouting. No client installs. It’s still direct SSH for your teams but with zero pre-auth attack surface.