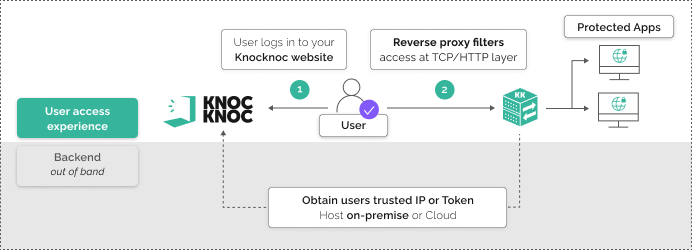
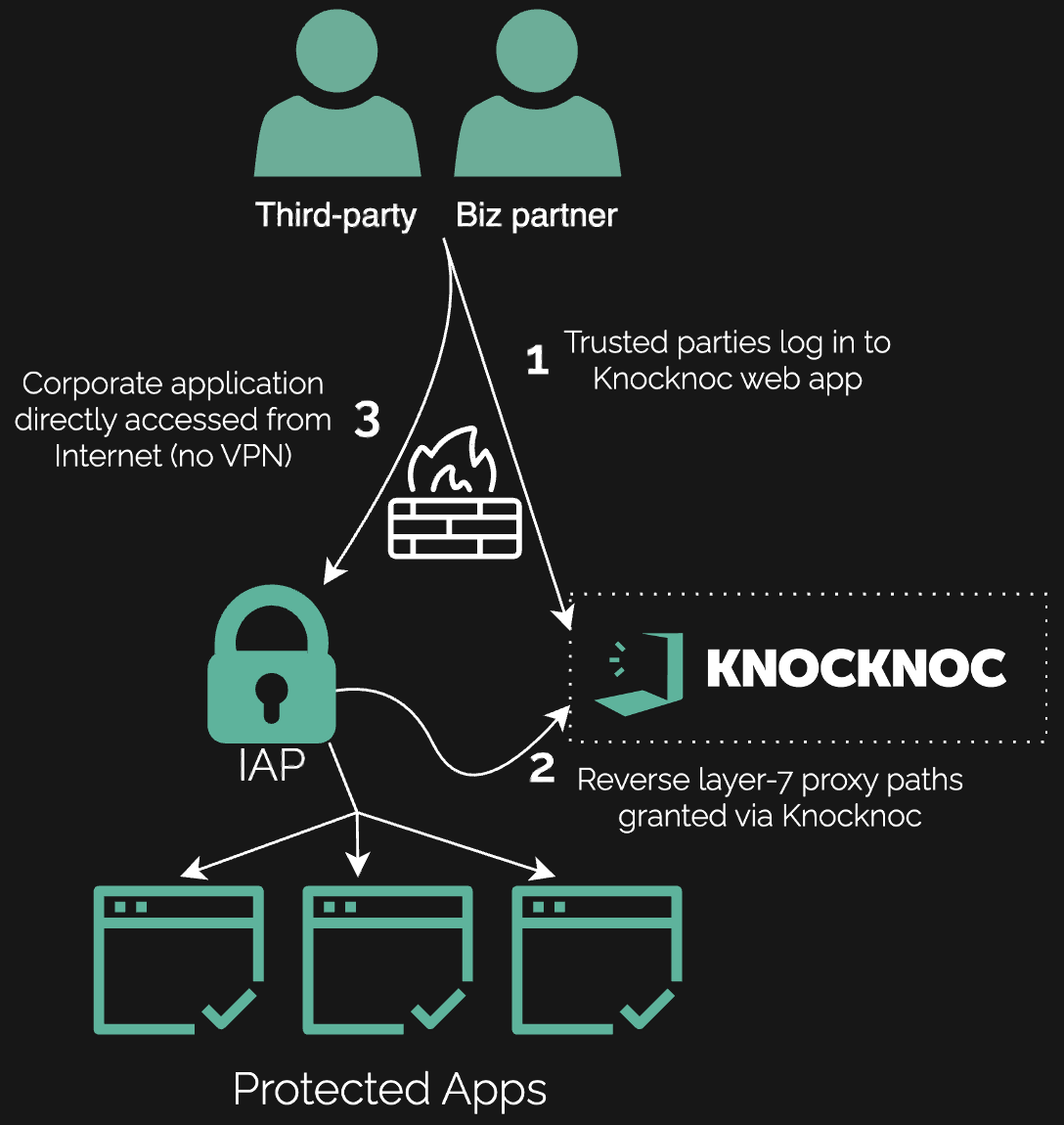
Even well-maintained web apps are risky when exposed. Knocknoc acts as a gateway: no one sees the app until they authenticate; then access is granted with filtering and control at layer-7, or L3/L4, all without a user/endpoint installation. Partner portals, sensitive data sharing platforms, dashboards or applications for corporate or partner use, but not general public access – why risk having them Internet exposed pre-authentication?
A financial services firm ran a partner upload portal for proprietary investment data. Patching and vulnerability awareness was a constant focus, but due to the proprietary and highly valued information, the CISO pushed to remove raw Internet exposure altogether.
The firm had to secure the app without breaking external partner workflows, which used unmanaged devices and at times low-signal mobile links.
Two patterns were used:
- Knocknoc in reverse-proxy mode restricting authorised paths to authenticated users only.
- Network allowlisting for scenarios needing direct access (e.g., Azure NSGs).
Both preserved a direct experience for partners; no client software was required.
The portal disappeared from public scans; partner experience stayed smooth; risk calculations eased. In one media customer, when CVEs later emerged on a file-transfer gateway, Knocknoc’s invisibility significantly reduced exploitability and the resulting risk given the exposure-window was effectively near zero.
Rollout continues across other legacy applications and embedded UIs. For apps that can’t do SSO, Knocknoc adds MFA/SSO without code changes, enabling fast attack prevention without application change.
Make sensitive web apps, path-level protection like “/admin”, and APIs invisible until SSO/MFA. Use Knocknoc as a reverse proxy (L7) or network allowlist (L3/L4). Partners keep a direct, no-client-install workflow; attackers lose the target entirely.