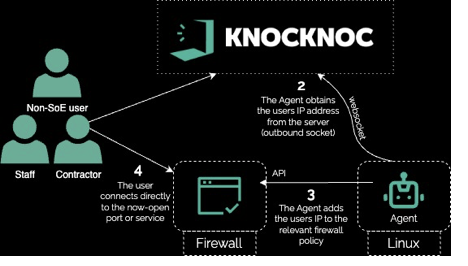
Internet-exposed VPNs are still top targets for brute-force, stolen creds, and appliance zero-days. Knocknoc turns your existing VPN from “always visible” into just-in-time: hidden until a user authenticates out-of-bound, then dynamically allowlists it open. No new client install, no change to your routing, no cloud or third-party transit risk.
A mid-size financial services firm relied on VPNs for staff, partners, and contractors. Legacy accounts still used single-factor. A credential-stuffing incident escalated into ransomware, triggering regulator scrutiny and concerning partners.
They needed to fix the edge fast without rolling out new clients to unmanaged devices or changing network paths.
Knocknoc sat beside their existing firewall, making the VPN invisible until after IdP authentication; then the user’s IP was allowlisted in an existing firewall policy, all automatically. No policies were added or changed, instead only the IP address list utilised by the firewall policy.
Brute-force noise stopped immediately; the VPN disappeared from scans. MFA adoption jumped; everyones confidence returned.
The firm extending Knocknoc to protect third-party app access to standardise edge hardening across all remote and partner services.
Exposed VPNs are ransomware magnets. Knocknoc hides them until after an out-of-band SSO/MFA, then allowlists the user’s IP for a short window. No client install, no routing change, no cloud transit, suitable for unmanaged devices. For users it’s seamless; for attackers it’s gone.
<< new diagram ? >>
