Many legacy/embedded UIs can’t do SSO/MFA, or worse they still use shared passwords. Knocknoc’s reverse proxy adds modern identity (and can control path-level access, like “/admin”) without touching app code or forcing a desktop/agent installation.
A logistics group ran warehouse equipment portals that auditors kept flagging (shared credentials, no MFA). Re-platforming wasn’t feasible.
The group had to modernize authentication and remove pre-auth exposure without code changes or material downtime.
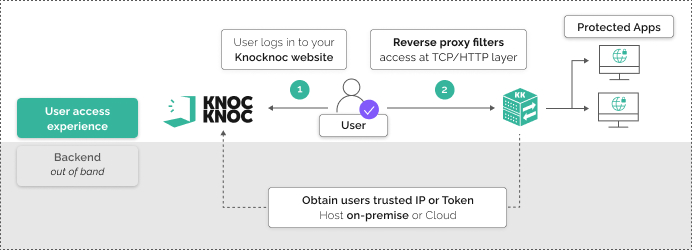
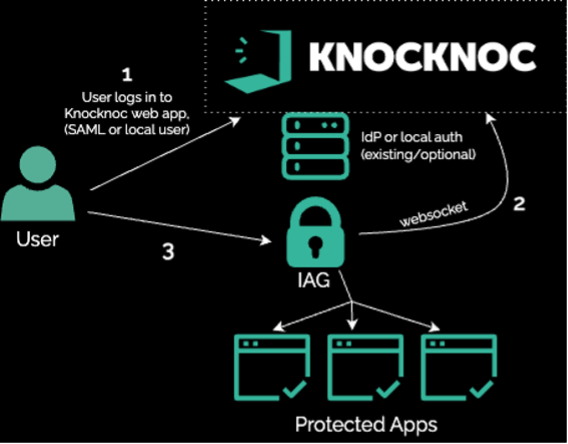
Knocknoc operated in reverse-proxy mode, linking inbound web traffic to the host through to identity. Users first authenticate via the IdP; only then does Knocknoc expose the otherwise protected applications. The web app’s static credentials stay hidden from users; Knocknoc can also combine identity with token checks and IP trust as needed to restrict when IP addresses are shared or the network is heavily NAT’d.
Legacy apps gained SSO/MFA and user-level attribution overnight; /admin and sensitive routes no longer existed to scanners; material risk was reduced.
The same pattern is being rolled out across small vendor boxes that can’t be patched quickly all protected by an identity-first perimeter.
Give legacy apps modern security without rewriting. Knocknoc requires SSO/MFA before exposure, keeps static credentials hidden, and can pair identity with tokens/IP address trust.
This can be achieved at various layers with Knocknoc
- Reverse proxy mode for TCP or HTTP/s – drop Knocknoc in, giving users feedback when they aren’t logged in
- Firewall mode – silently drop packets, so attackers don’t even know the system exists