How Knocknoc Works
Keep ports closed and services hidden until users log in. Knocknoc dynamically updates access controls, eliminating attack surfaces without disrupting your existing architecture.
SSH
Knocknoc dynamically adds user IPs to your IPTables/IPSet allowlist after central authentication. Enjoy zero network exposure with just-in-time firewall control tied to MFA or your identity platform.
Hosted Apps
Eliminate direct internet access for legacy or high-risk systems. Knocknoc securely exposes them only after login, with options for layer-7 filtering or complete firewall-based access control.
Low Latency Access
Access services directly without VPNs or extra routing. Once authenticated, user IPs are allowed, enabling direct connections without centralized dependence or client configuration.
VPN & Firewall Devices
Secure management interfaces or protect VPN services from brute-force attacks. Knocknoc reduces exposure to zero-day attacks by requiring central login before network exposure.
Features of Knocknoc
Simplify access control for your networks.
- Not a VPN, not a Cloud: A unique approach to network control infrastructure - novel, elegant, and highly effective.
- Use Your Existing Infrastructure: No additional devices, routes or latency; complete control over direct network access without relying on VPN-like services.
- Timed Access Control: Grant access only when users are authenticated and within predefined timeframes, access management made simple.
Leverage advanced authentication to strengthen security.
- Zero Trust: Ensure no one gains access without authentication. Knocknoc simplifies the zero-trust model - just “Knoc first.”
- Enhanced Security: Zero your attack surface and eliminate brute force attempts.
- Authenticated Integration: Compatible with platforms like Okta, Entra, Google, Jumpcloud, Authentik, or as a standalone system, with built-in MFA for added protection.

Simple to deploy, effortless to use.
- Seamless Integration: Easily add SAML and MFA to non-native applications like SSH, RDP, network controls or raw video feeds, at no added cost.
- Visibility and Audit Trail: Full visibility into authenticated users, access windows, and durations with a robust activity audit trail.
- Highly extensibile: Integrate authorized logins with ACLs, transforming Identity Groups into ACLs across your systems.
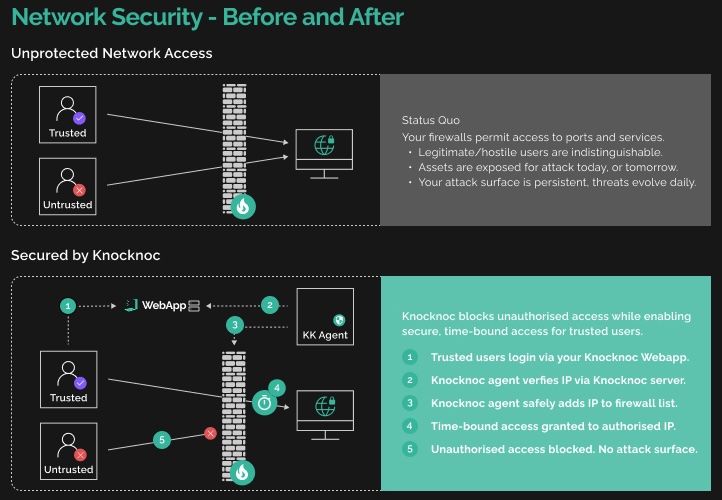
How Knocknoc Eliminates Attack Surfaces
Knocknoc redefines security by dynamically implementing just-in-time network and application allow-listing. It doesn’t just mitigate risks – it makes attack surfaces disappear.
Knocknoc dynamically implements just-in-time network and application allowlisting to make attack surfaces disappear.
The solution’s flexibility means it can dynamically orchestrate network access controls (e.g., managing firewall rules in real-time without exposing target machines) or function as an identity-aware gateway. You can choose the configuration that fits your needs – or combine both for maximum impact.
Here’s how Knocknoc works: when a user successfully logs in via Knocknoc’s centralised portal, the system dynamically provisions their IP address to the network’s access control layer.
Knocknoc isn’t a proxy or VPN – it’s a control layer that you can host yourself or let us host for you. It supports all major access control systems, from commercial firewalls to public cloud providers, even offering custom scripting capabilities for unique setups.
Take a typical SSH bastion host:
- Without Knocknoc: SSH is exposed to the entire internet, allowing any IP to probe the port, exposing the network and service stack to potential attacks.
- With Knocknoc: An agent dynamically opens the SSH port only for the authenticated user’s IP address, after they’ve logged into the Knocknoc portal. Until then, no port or service is visible, effectively removing the attack surface.
But Knocknoc doesn’t stop there. If you need to shield VPN services on devices provided by companies like Fortinet, Palo Alto, or Ivanti, Knocknoc can orchestrate their protection, removing them entirely from the internet until authenticated access is granted. Today’s attack surfaces are potential vulnerabilities for tomorrow’s zero-day exploits – Knocknoc ensures they never see the light of day.
Ready to dive deeper? Read our documentation here.
Can Knocknoc Replace My VPN?
It can, but why not have both? Knocknoc goes beyond VPN functionality while also operating alongside one.
In many cases, Knocknoc complements your existing VPN. While traditional VPNs often secure internal resources for staff, site-to-site connectivity, or administrative workloads like non-HTTP protocols, VPNs remain exposed to the internet. Knocknoc changes that. By orchestrating access, it ensures your VPN isn’t exposed until users first authenticate through your Knocknoc portal, dramatically reducing its attack surface, removing brute-force attacks, infiltration using stolen credentials, or vulnerabilities in the VPN platform itself.
Knocknoc also shines where VPNs fall short. It’s ideal for contractors, third parties, users outside your standard operating environment, or scenarios requiring faster, more direct access to resources – like development and test environments, legacy or custom web apps.
Moving these behind a VPN is often too complex or presents other weaknesses to your environment, so organisations choose to leave them exposed. Knocknoc provides the security you need without requiring considerable time and effort .
Unlike many VPN and ZTNA solutions, Knocknoc doesn’t require a client installation, keys or VPN configurations, making it far more approachable to users, third-parties and diverse or unmanaged-device environments. Plus, it doesn’t broker or touch your network traffic, ensuring low latency and high security.
No added complexity. No risk of third-party traffic observation. Just direct, secure access.
Hosted on-premise or in your Cloud, but importantly: in your complete control.
How Do I Deploy Knocknoc?
1
Deploy Your Knocknoc Server
Begin by setting up the Knocknoc server, which serves as the central hub for both users and administrators. It provides the web interface and integrates with your identity provider. Knocknoc can be deployed on-premise within your network or hosted infrastructure, or in our managed cloud.
2
Deploy an Orchestration Agent
Once your server is running, deploy one or more Knocknoc agents. These agents connect to the server, receive instructions to allow or deny IP addresses (both IPv4 and IPv6), and enforce access rules for backends within their reach based on user mappings.
3
Define Your Backends
- Linux Firewalls: e.g., ipset, iptables, UFW, Shorewall, etc.
- Firewall Appliances: Fortinet, Palo Alto, Checkpoint, Ivanti, etc
- Reverse Proxies: HAProxy, Nginx
- Cloud ACLs: e.g., AWS Security Groups, Entra Conditional Access
- Many more options
Need something more flexible? Knocknoc has you covered with a “script” backend. This enables you to create custom integrations, such as controlling network interfaces, managing services like hostapd, enabling/disabling serial interfaces, or anything else you can think of.