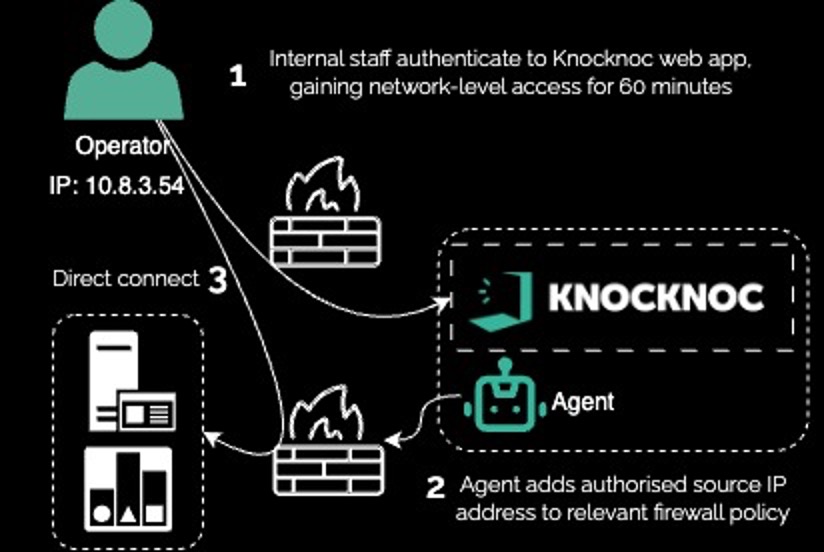
Critical networks must be default-deny yet still allow operator work, ideally as direct as possible. To solve this, Knocknoc grants short-lived, attributable network-level access windows after centralized login (e.g., 60 minutes), with the network snapping back to invisible. Operators can move quickly, attackers are blind, auditors see strong controls.
A water utility segmented management networks and OT jump hosts into high-security zones. Government authorities were ringing the alarm bell; shields up, critical infrastructure is a real focus of attack. Yet engineers still needed access to various high-security subnets and assets for maintenance and their business as usual day jobs.
Permanent and always-on network exposure undermine segmentation. Manual firewall changes weren’t scalable and broad network access was simply a necessity for some higher-privilege users. The environment needed automated, time-boxed access that preserved default-deny at all other times.
Knocknoc was integrated with the existing firewall appliances. When an operator authenticated via the corporate IdP, Knocknoc opened a 60-minute window to the target subnet, then automatically removed access on logout or timeout. No endpoint agent software was installed, no additional VPN, up and running fast.
Sensitive internal networks stayed invisible 99% of the time; operators gained fast, auditable paths exactly when needed. Insider risk fell, network noise and lateral movement risk was reduced, thanks to time-bound, user-attributed network access records.
The organisation is scaling the pattern to control networks and other more sensitive segments, the same “log in → get minutes of reachability → auto-revoke” everywhere.
High-security subnets should be off and invisible by default. With Knocknoc, operators log in, receive a short, audited network-level access window, then everything auto-closes. It’s the practical way to apply just-in-time network access without a major re-architecture or end-client software install.
This is also used for egress control, not just ingress. Allowing organizations to time-box networks reaching out for updates, control third-parties or control other just-in-time network flows.