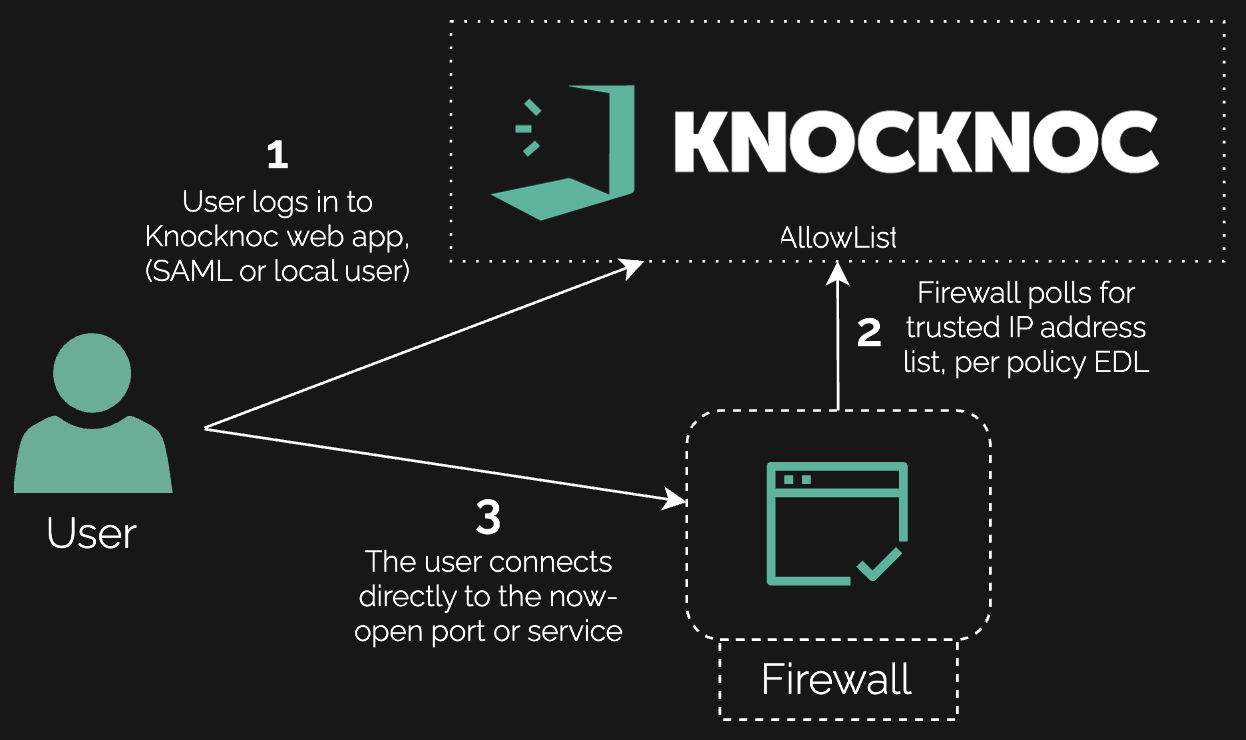
When the firewall itself is the target, exposure must be zero by default. Knocknoc hides management and VPN interfaces until after authentication via Active API orchestration, Passive EDLs, or Passive+ (EDL with live refresh), fitting different vendors and change/risk models.
An enterprise operating Fortinet and Palo Alto fleets dreaded the next zero-day advisory. Remote management was essential for SLAs, but consoles on the Internet or internal networks were uncomfortable for engineers, customers and security teams alike.
The organizations goal was to retain fast remote admin while removing the standing exposure.
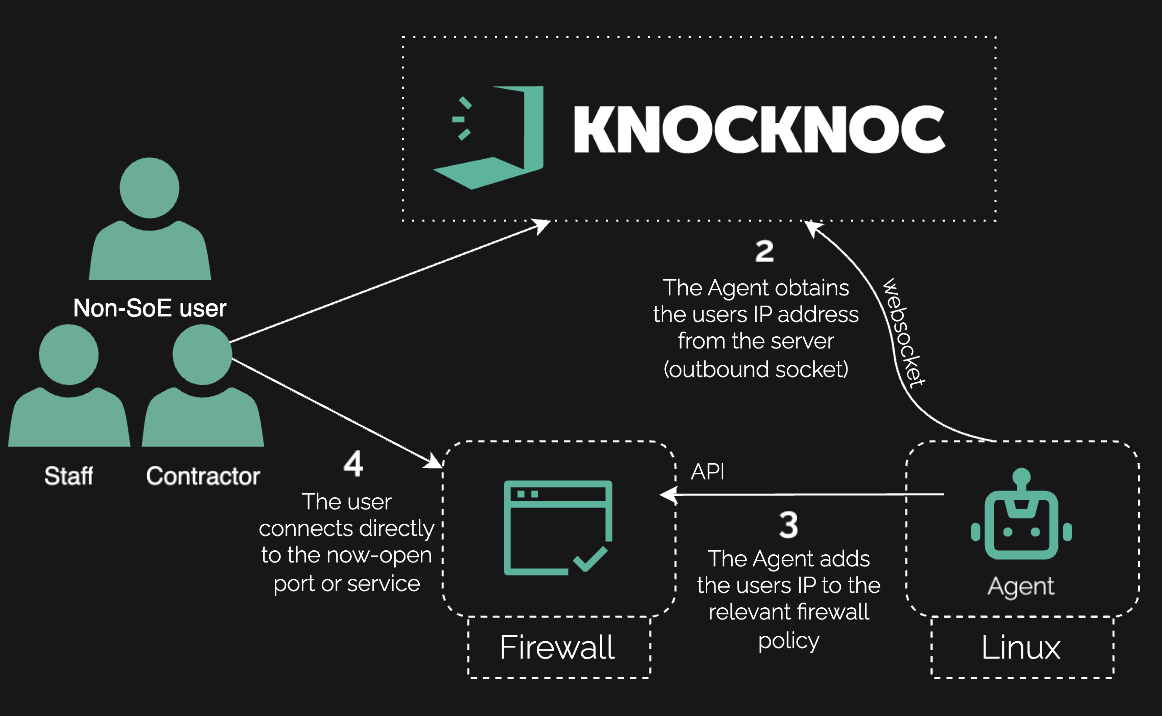
Knocknoc updated allowlists dynamically only after engineers authenticated via the IdP, either writing to device policies through APIs (Active) or publishing allowlists for the devices to pull (Passive/EDL), with a Passive+ mode to trigger immediate refreshes where commit cycles are slow due to firewall complexity.
Interfaces vanished from scans; engineers kept their speed; zero-day worry turned into calm patching cycles. The pattern also protects SSL VPN surfaces until the user is authenticated.
The organization is standardizing the model across vendors and hybrid edges to make “invisible until authenticated” the default for any admin or remote-access surface, and higher-risk internal admin interfaces.
Protect the protector. Knocknoc keeps firewall/VPN interfaces invisible and exposes them only to authenticated engineers for a short period of time.
Agentless deployment can be established using the Allowlist feature: